Sometimes it’s best to illustrate power when we put it to numbers and all we’re going to say is that at the present moment there are over 400 million users of Windows 10 alone.
The other fact that there isn’t a precise number determining how many Windows users there are in the world speaks volumes of just how popular Microsoft really is.
Chances are that you’re reading this article from your Windows operated device and if so, then you’re here to find out more about taking you Windows Protection to the next level.
There are many ways to get around protecting your Windows operating system and many of them depend on which Windows you use and how much you know about online security.
We’ll share with you five tips that can be applied to practically any Windows you have to ensure its protection.
How To Achieve Maximum Windows Protection:
1. You Need Your Backup System

One of the first things you should do to enhance your Windows protection is to have a backup plan or, to be more exact, to have a working backup system.
Prevention is the best thing you can do when it comes to your online security. Doing regular backups of your most valuable information is one way to be sure that everything crucial is kept safe at all times.
Sometimes problems don’t come from the outside but happen within your hardware and there’s no security software to keep you safe from these troubles.
There are many big name companies that offer excellent solutions for backing up your data and all you need to do is take your pick. You should also think about how you want to secure your files – an online cloud or external hard-drive?
There also a few rules to remember – have three copies of all important information on different types of backup support, make sure that the files are safe with strong passwords and set up your backups to be done automatically so that you don’t have to worry about them.
2. Antivirus Program and Firewall
You probably know that having an antivirus program is one of the first things you need to do to keep your internet security in check.
It’s quite easy to find antivirus these days, seeing that there are many strong security companies that offer their services both for free and for a fee.
All you need to do is establish what level of protection you need because free versions of antivirus programs will cover some basic security levels, but if you need more than that, you’ll have to pay to make sure your security status is good.
Also, check to see if your chosen antivirus comes with a firewall, which is a very important component of your internet shield.
If the firewall is not a part of package deal, you can always resort to Windows Firewall, which will do a decent job in protecting your OS from outside threats.
3. Against Malware and Spyware
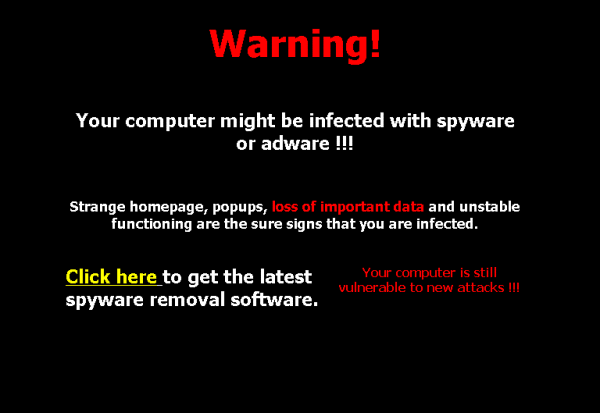
 You may need an additional level of protection against the latest forms of malware and specifically spyware, which is becoming more and more annoying with each passing year.
You may need an additional level of protection against the latest forms of malware and specifically spyware, which is becoming more and more annoying with each passing year.
Changing your default browser, showing popup ads everywhere, redirecting your every search to malware riddled websites – this is the chaos that goes with spyware.
Some particularly nasty forms can even track your internet activities and use these records against you by stealing your financial details or your identity.
This is why you should also have strong anti-malware installed on your Windows and why most of us must use VPN (virtual private networks) to keep under the radar of surveillance and hacker tracking.
Believing you’ve got nothing to hide won’t save you from cybercriminals that are able to use even the smallest piece of information to disable your security systems.
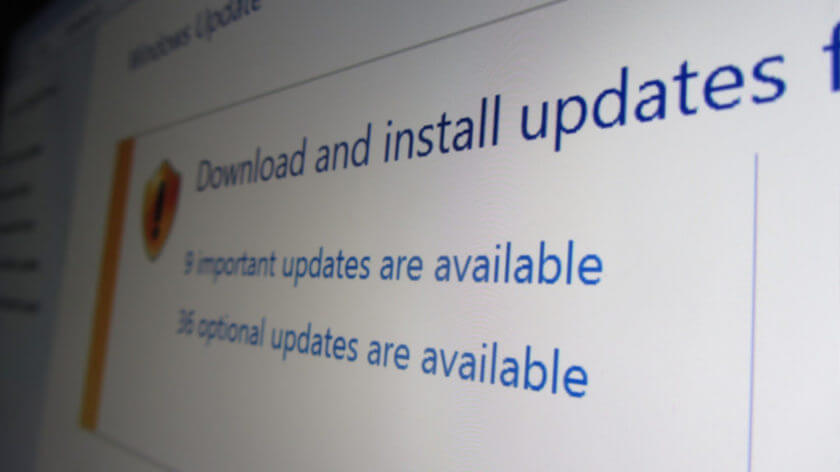
4. OS and Software Should Always Be up to Date
Updates exist for a very good reason and that is to keep all the potential holes in your security patched regularly. That is why updates are fairly frequent and why you shouldn’t be irritated by them, even though they can be unwelcome.
The truth is that both your operating system and pieces of software you use should always be up to date, otherwise black-hat hackers will take full advantage of them and infect your Windows with gods know what. It would be wise to let both your system and your software update automatically so that you don’t have to handle everything manually.
It would be wise to let both your system and your software update automatically so that you don’t have to handle everything manually.
Also, take a closer look at what software you actually use and what just lingers around in your system, slowing it down unnecessarily. Whatever you don’t need, you should promptly get rid of to improve your device’s performance and security.
5. Use Your Restore Option
 As soon as you install your Windows (enter number here) you should set restore point where you can have clean installation you can go back to in case something endangers your OS. This is yet another smart precaution you should
As soon as you install your Windows (enter number here) you should set restore point where you can have clean installation you can go back to in case something endangers your OS. This is yet another smart precaution you should
This is yet another smart precaution you should take, because this restore point will get you back to square one of your system, before any potentially problematic programs were installed. As you can see, you should always have a failsafe (or a few) to get your Windows on track faster, and you can be sure that clean installation
As you can see, you should always have a failsafe (or a few) to get your Windows on track faster, and you can be sure that clean installation restore point is going to work.
Protecting your Windows both online and offline is not a one-time thing. Security is not an exact science, which means that you will always have to work on improving it, sometimes a bit more, sometimes a bit less. The catch is never to let anything slide, if something looks suspicious, check it out, it’s better to be safe than sorry.
The catch is never to let anything slide, if something looks suspicious, check it out, it’s better to be safe than sorry.
About The Author:
Thomas Milva has been in the business of information security for four years, and strongly believes that he picked the best timing for his profession, which he often underlines in his articulate articles for wefollowtech.com. Most of the time, he works from home, and whenever he’s free, he organizes hikes for his dog, his girlfriend and himself. Tom’s home, for the time being is Baton Rouge.



















 You may need an additional level of protection against the latest forms of malware and specifically spyware, which is becoming more and more annoying with each passing year.
You may need an additional level of protection against the latest forms of malware and specifically spyware, which is becoming more and more annoying with each passing year.
 As soon as you install your Windows (enter number here) you should set restore point where you can have clean installation you can go back to in case something endangers your OS. This is yet another smart precaution you should
As soon as you install your Windows (enter number here) you should set restore point where you can have clean installation you can go back to in case something endangers your OS. This is yet another smart precaution you should